iBGP - BGP within AS4242423905
For a better understanding here are the picture of my iBGP Mesh:
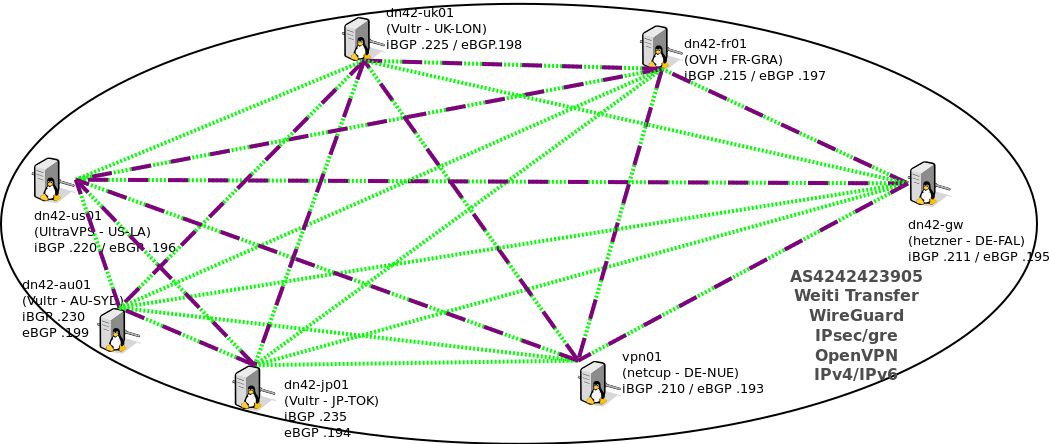
Every Peering has its own Bird Routing Table and i use pipes to leak from the Peering Tables to master. Following are the details of my iBGP Peerings/Templates and Filters. The lines indicates WireGuard VPN Links (purple) and iBGP Peerings (green dotted).
Used Bird Templates for iBGP Peerings and Pipes
# Template for iBGP Peerings
template bgp iBGP_Peer {
local as MYAS;
# Table should be set within each Peer to T_PEERNAME
igp table T_OSPF;
path metric on; # Enable comparison of path lengths when deciding which BGP route is the best one
import keep filtered; # Keep Filtered Routes for this peering.
import where iBGP_import_peer_policy(); # iBGP Import Peer Policy
export where iBGP_export_peer_policy(); # iBGP Export Peer Policy
source address MYIPv4; # iBGP Peering with MYIPv4 to add backup pathes
next hop self; # Set Next Hop Self for clean routing
};
# Template Pipe for iBGP Peerings
template pipe iBGP_Pipe {
# Table had to be set in each Peer Definition to T_IBGP_PEERNAME
peer table master;
import where iBGP_routing_policy();
export where iBGP_routing_policy();
};With these Templates, a iBGP Peering consists of one file in peers4/6 directory, for example Peering Definition on dn42-uk01 for dn42-de02 aka dn42-gw:
table T_IBGP_DE02;
protocol bgp B_IBGP_DE02 from iBGP_Peer {
table T_IBGP_DE02;
neighbor 172.20.175.211 as 4242423905;
};
protocol pipe P_IBGP_DE02 from iBGP_Pipe {
table T_IBGP_DE02;
};BGP Communities for AS4242423905
I added the following communities to routes i learned:
| BGP Community | Desription |
|---|---|
| MYPeerID | PeerID of System who learns the route( PeerID == iBGP Loopback IP) |
| 1000 + MYPeerID | Peering Originates from an Peer on System with PeerID |
| 7000 + MYPeerID | Route was learned from a "Customer/Peering" on System with PeerID |
| 8000 + MYPeerID | Route was learned from an IXP on System with PeerID |
| 9000 + MYPeerID | Route was learned from an "Upstream" on System with PeerID |
.
Based on this communities i update local_pref on iBGP egress per System. Below you find my current Filter/Routing Polica on iBGP Links.
iBGP Routing Policy and import/export filter
#
##
## iBGP Policies
##
#
# iBGP Peer Policies
function iBGP_import_peer_policy() {
if bgp_path.len > 64 then return false; # Reject too long BGP Paths
if local_nets() then return false; # Reject local used networks (IXP, Peerings) from iBGP Peers
if ( bgp_local_pref > 1000 ) then { # Reset local pref on iBGP Links, to do AS Path Metric only
bgp_local_pref = 100;
}
return true; # Allow all on iBGP Links
};
function iBGP_export_peer_policy() {
if proto = "dn42_static" then return true; # Allow Static announced routes, should be renamed to S_STATIC
if source != RTS_BGP then return false;
if bgp_path.len > 64 then return false;
if ( bgp_ext_community ~ [ (rt, MYAS, MYPeerID + 9000 ) ] ) then {
bgp_local_pref = 100;
}
if ( bgp_ext_community ~ [ (rt, MYAS, MYPeerID + 8000 ) ] ) then {
bgp_local_pref = 110;
}
if ( bgp_ext_community ~ [ (rt, MYAS, MYPeerID + 6000 ) ] ) then {
bgp_local_pref = 115;
}
if ( bgp_ext_community ~ [ (rt, MYAS, MYPeerID + 7000 ) ] ) then {
bgp_local_pref = 145;
}
return true; # Allow all on iBGP Links
};
# iBGP Routing Policies
function iBGP_routing_policy() {
if source = RTS_OSPF then return false; # For iBGP i don't want OSPF in my Routing Policy
if source = RTS_DEVICE then return false; # For iBGP i don't want DEVICE ROUTES in my Routing Policy
krt_prefsrc = MYIPv4;
return true; # Allow all on iBGP Links
};